
Blind Insight
Cloud-based and on-premise data privacy platform that offers searchable encryption and access controls through an API-driven approach.
What is Blind Insight?
Blind Insight is a data privacy and security software that provides real-time searchable encryption and fine-grained access controls to protect sensitive data. The API-driven platform analyzes encrypted data without decrypting it using proprietary encryption-in-use technology. It enables SQL-like operations on encrypted data at high speeds. Blind Insight's offers developer-friendly APIs and SDKs to enforce and monitor data access controls, track query patterns, integrate with databases, and customize field-level permissions.
Screenshots

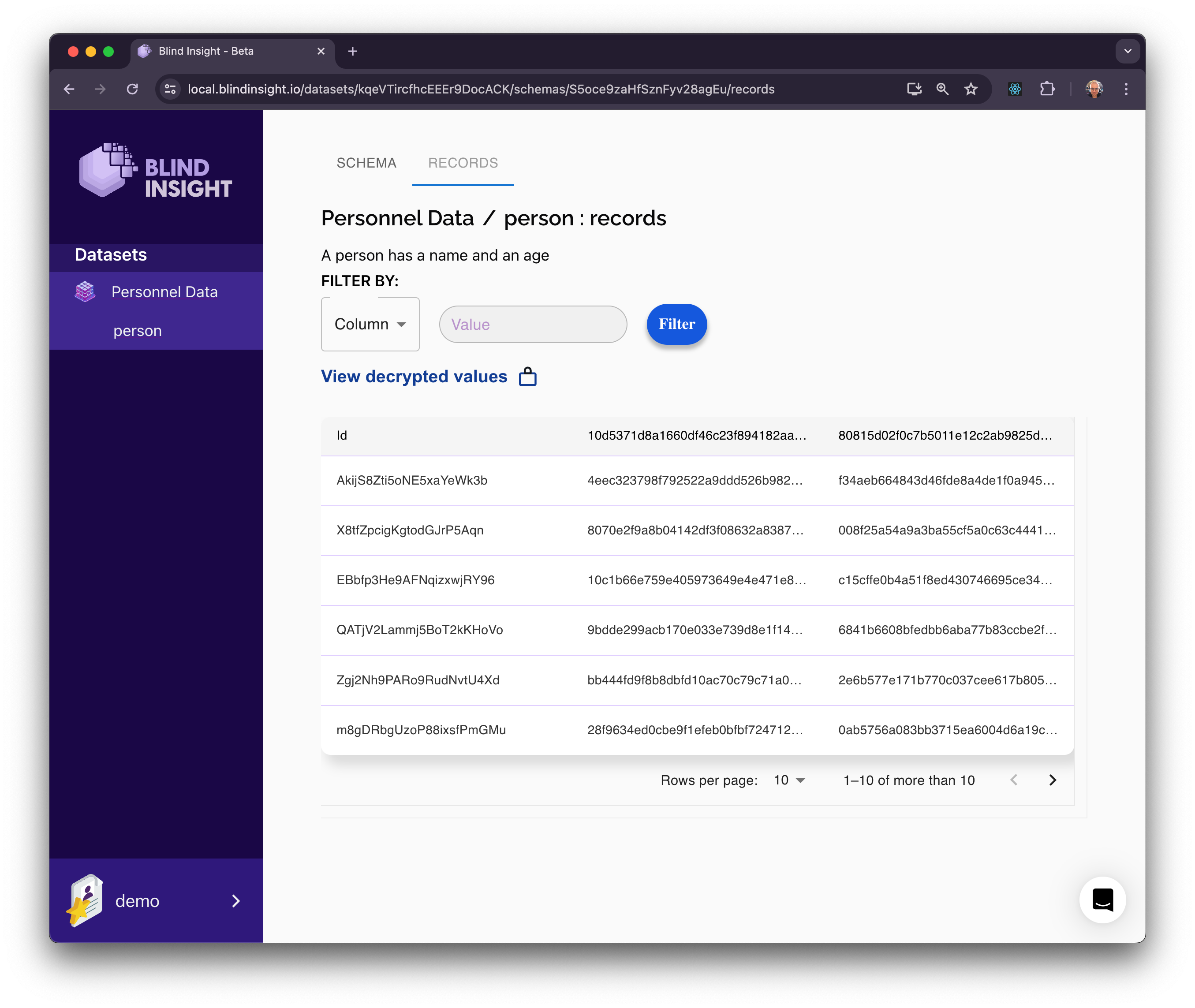
Video
Features
FAQ
Blind Insight is a data privacy and security software that provides real-time searchable encryption and fine-grained access controls to protect sensitive data. The API-driven platform analyzes encrypted data without decrypting it using proprietary encryption-in-use technology. It enables SQL-like operations on encrypted data at high speeds. Blind Insight's offers developer-friendly APIs and SDKs to enforce and monitor data access controls, track query patterns, integrate with databases, and customize field-level permissions.
Blind Insight belongs to the Data Governance, Data Privacy category.
Blind Insight offers features such as Access Controls/Permissions, Data Discovery, Data Mapping, Data Profiling, Deletion Management, Compliance Management, Data Security, Data Subject Requests (DSR/DSAR), GDPR Compliance.
No, Blind Insight does not offer a free trial.
Pricing
Starting at:
$25/free plan
Free Trial Available
Reviews(0)
Write a reviewBlind Insight alternatives

Google Cloud
Google Cloud Platform is cloud-based suite of solutions that allows users to create anything from websites to complex applications for businesses of all sizes across a range of industries. Google Cloud Platform offers a scalable data warehouse powere...load more

Oracle Database
Oracle database services and products offer customers cost-optimized and high-performance versions of Oracle Database, the world's leading converged, multi-model database management system, as well as in-memory, NoSQL and MySQL databases. Oracle Auto...load more

MongoDB
MongoDB is a modern document model (NoSQL) database that provides unmatched flexibility, scalability, and reliability for managing dynamic and evolving data. Designed to handle structured, semi-structured, and unstructured data, its dynamic schema su...load more

Logi Symphony
Logi Symphony solves business intelligence's core problem: users shouldn't leave their workflow for insights. Our platform embeds powerful analytics directly into existing applications, eliminating friction that kills BI adoption. Perfect for softwar...load more

CrashPlan
CrashPlan provides cyber resilience and data protection through a unified platform trusted by organizations worldwide. With secure, scalable backup and recovery for servers, endpoints, Microsoft 365, and Google Workspace, CrashPlan safeguards critica...load more

Tresorit
Tresorit is an end-to-end encrypted file sync and sharing solution designed to safeguard sensitive content. Unlike other public cloud vendors, Tresorit has no access to user files, which ensures maximum confidentiality. - Files are protected from the...load more

Egnyte
Egnyte is a cloud content collaboration platform that provides secure file sharing, access governance, compliance tools, and content intelligence. The software enables businesses to manage, protect, and optimize critical content across any cloud, app...load more

Alteryx Designer
Alteryx Designer is a desktop-based self-service data profiling, preparation, blending, and analytics product used to create visual workflows or analytic processes through an intuitive drag-and-drop interface. In addition to dramatically reducing the...load more

Snowflake
Snowflake empowers the Data Cloud, fostering global data connectivity and collaboration across diverse scales and types.

Teramind
Detect and block insider data exfiltration with behavior analytics, zerorust controls, realime intervention, and forensic readiness